Understanding SQL Injection Attacks
In the dynamic field of cybersecurity, SQL injection (SQLi) poses a significant and menacing threat to web applications. At Hackzap Security, we recognize the critical importance of protecting digital assets from such malicious exploits. This article delves into the complexities of SQL injection attacks, revealing their mechanisms, consequences, and methods for mitigation.
What is SQL Injection?
SQL injection is a type of cyber attack that targets web applications by injecting malicious SQL code into input fields or parameters. These inputs are typically designed to interact with a backend database, such as MySQL, PostgreSQL, or Microsoft SQL Server. By exploiting vulnerabilities in poorly sanitized user inputs, attackers can execute arbitrary SQL commands, bypass authentication mechanisms, extract sensitive information, and even gain unauthorized access to the underlying system.
How Does SQL Injection Work?
Imagine a scenario where a web application uses SQL queries to authenticate users:
SELECT * FROM users WHERE username = 'input_username' AND password = 'input_password';An attacker can manipulate the input fields to inject malicious SQL code, such as '' OR '1'='1', altering the query to:
SELECT * FROM users WHERE username = 'input_username' AND password = '' OR '1'='1';This modified query always evaluates to true ('1'='1'), granting unauthorized access to the application.
Types of SQL Injection
SQL injection attacks manifest in various forms, each with distinct objectives:
- In-band SQL Injection: Also known as traditional or classic SQL injection, this type involves using the same communication channel to both launch the attack and retrieve the results. In-band attacks can be further categorized into:
- Error-based SQL Injection: Exploiting error messages generated by the database to extract information about its structure or contents.
- Union-based SQL Injection: Leveraging the UNION SQL operator to combine the results of two separate queries, allowing attackers to extract data from other tables.
- Blind SQL Injection: In scenarios where error messages are not directly accessible, blind SQL injection techniques are employed to infer information indirectly. This can be achieved through:
- Boolean-based SQL Injection: Manipulating conditional expressions in SQL queries to discern true or false responses.
- Time-based SQL Injection: Introducing time delays in SQL queries to infer the success or failure of injected conditions.
- Out-of-Band (OOB) SQL Injection: Unlike in-band attacks, OOB SQL injection exploits alternate channels, such as DNS or HTTP requests, to exfiltrate data or communicate with the attacker's server. This approach is particularly useful when direct retrieval of results is not feasible.
Examples of SQL Injection Attacks
Consider the following scenarios demonstrating SQL injection vulnerabilities:
- Basic Authentication Bypass:
An attacker enters' OR '1'='1in the password field, bypassing authentication checks and gaining unauthorized access. - Data Extraction:
By injecting105 OR 1=1into the input field, the attacker crafts a query to retrieve all user data from the database. - Dropping Tables:
Injecting105; DROP TABLE Suppliersexploits batched SQL statements, executing additional malicious commands.
Mitigation Strategies
Protecting against SQL injection requires a proactive approach:
- Parameterized Queries: Use parameterized queries to separate SQL code from user input, preventing injection attacks.
- Input Validation: Implement strict input validation to filter and sanitize user inputs, rejecting unauthorized data.
- Least Privilege Principle: Assign minimal permissions for database access, limiting the impact of successful attacks.
- Web Application Firewalls (WAF): Deploy WAF solutions capable of detecting and blocking suspicious SQL injection attempts.
- Regular Audits and Penetration Testing: Conduct comprehensive security audits and penetration tests to identify and remediate vulnerabilities.
Example of Secure Coding Practices
Implementing parameterized queries in PHP:
$stmt = $dbh->prepare("INSERT INTO Customers (CustomerName, Address, City) VALUES (:nam, :add, :cit)");
$stmt->bindParam(':nam', $txtNam);
$stmt->bindParam(':add', $txtAdd);
$stmt->bindParam(':cit', $txtCit);
$stmt->execute();Conclusion
SQL injection remains a potent threat to web application security, capable of wreaking havoc on databases and compromising sensitive information. At Hackzap Security, we advocate for vigilance, education, and robust security measures to defend against such attacks. By understanding the intricacies of SQL injection and implementing best practices, organizations can fortify their defenses and safeguard their digital assets against malicious exploitation.
Additionally, it's essential to recognize that SQL injection attacks can be performed using various tools, such as sqlmap, Havij, and SQLNinja. These tools automate the process of detecting and exploiting SQL injection vulnerabilities, making it easier for attackers to compromise systems. However, at Hackzap Security, we prioritize ethical security practices and do not endorse or support the use of such tools for malicious purposes.
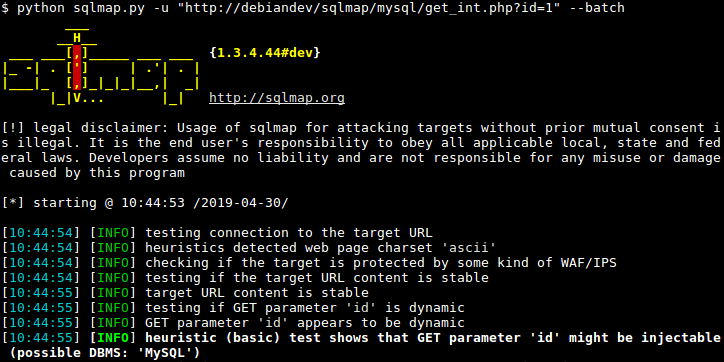
In the next upcoming blog article on Hackzap Security, we will dive deeper into the usage of sqlmap, demonstrating how it can be employed by ethical hackers and security professionals to identify and mitigate SQL injection vulnerabilities in web applications. Stay tuned for actionable insights and practical demonstrations to bolster your cybersecurity defenses.
Thank you for reading!
Follow us on:
